When cybersecurity is discussed, a text editor is rarely the first to come to mind. It’s a simple but versatile piece of software that allows you to view, edit, and create text or code files—not much in terms of possible attack vectors. Fast forward to recent times, however, and you would find that companies cannot ignore hardening their software supply chain—which includes even the humble text editor.
In this article we discuss why a text editor like UltraEdit has placed an emphasis on security, and why it is even doubling its efforts to do so.
How is a software considered secure?
First of all, it is necessary to define what constitutes a secure software. A dictionary defines secure as “the state of being free from danger or threat.” In software, there is hardly a time when users or programs are not exposed to vulnerabilities—whether it comes from malicious actors or unintentional errors made by users themselves.
In that case, it may be prudent to consider that having security-hardened software does not mean that security attacks and dangers disappear; instead it describes the innate ability of a software application to resist and prevent the unnecessary damages from the inevitable dangers of cybercrimes.
In the case of UltraEdit, our working definition is as follows:
A software program can be considered security-hardened when it undergoes a comprehensive set of practices and measures to protect it against potential threats and vulnerabilities, during and after development.
The cybercrime scene and cybersecurity industry
Security is one aspect that is often overlooked when choosing text editors. The possible surface area of attack for a program run locally on a machine is arguably lesser than say, a cloud-based network system. This holds true for UltraEdit as much as it does for other developer tools.
However, trends in the software industry indicate an increasing reliance on software interdependence. New software is built upon both previous and current technology creating a web of software dependencies. The popularity of open source software and components have greatly accelerated the speed of development, reduced the outright costs, but has exponentially increased the potential surface area for attack as well.
This has prompted companies, businesses, and even the US government a campaign to move to zero trust models in order to curb potential open source threats and minimize the resources needed to alleviate damages from data breaches. To put this in perspective, the global average data breach cost was $4.35 million in 2022.
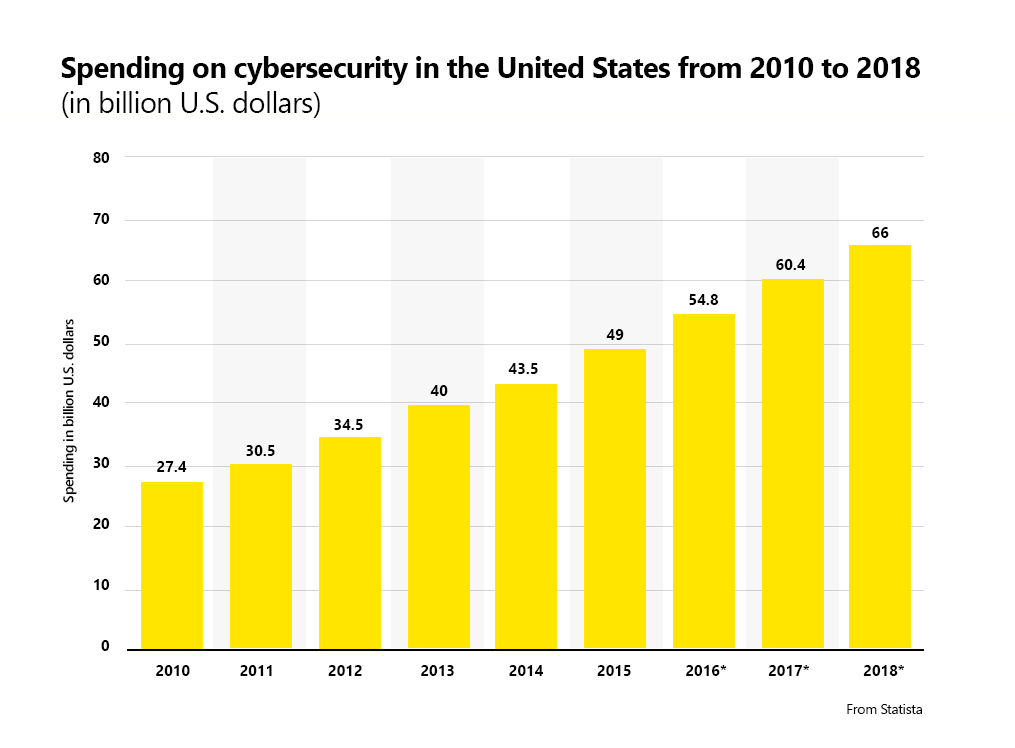
The Cybercrime Magazine reports that in 2004, “the global cybersecurity market was worth $3.5 billion” but in 2018, you can see that spending has dwarfed that almost eighteen times over at $66 billion.
Investments in cybersecurity, while on the rise, is a tricky subject for businesses. Most of a company’s budget for IT and software development is allocated for tools and training. It’s straightforward: investing more usually results in increased productivity; on the other hand, investing in cybersecurity can be harder to justify—it’s an apparent financial sinkhole with no apparent benefits until something does go wrong.
Read on further to learn more about threats and vulnerabilities in cybersecurity. Hopefully, if you are a business owner or a developer yourself, you will realize that the damages from a security breach will far outweigh the expenses of investing in even the most fundamental security fortifications.
Threats and vulnerabilities in text editors
Cybercrime takes on many forms: social engineering, network hacks, fraud, espionage, and a lot more. Each product or software in a business’ software supply chain should theoretically be as fortified as possible. It would not make sense to invest thousands of dollars on cloud security only for your system to be breached because you did not have multi-factor authentication for its employees in place.
Take for example a text editor that at its core serves a basic need of editing plain text data—it should be fairly simple to secure it and the data it edits, right? Yes, but be that as it may, the needs of users change and demands for more complex functionality dictate that the technology (and cybersecurity measures) has to evolve as well, thus the term software development. Text editors do more than just edit text nowadays (Lines blur between text, code editors, and IDEs). Auxiliary components such as HTML live previews, scripting and macros, and even hex editing may very well be considered essential.
This demand for extensibility has given birth to editor and IDE plugins—pieces of software created by the open source community that users can download from a plugin marketplace. Editor plugins and extensions provide exceptional flexibility and customizability to tailor fit any user’s specific use case. (This is so much so that UltraEdit is planning on creating its own ecosystem of plugins—more on this later).
However, plugins and extensions also greatly increase the breadth and scope of code that needs to be vetted for security, vulnerabilities, and potential development flaws. When using plugins, users waive some semblance of access to their source code in one way or another. To counter threats, plugin ecosystems and marketplaces establish guidelines and prerequisites before you are able to publish a plugin. Some ecosystems are more lax than others, while some require stringent processes before you are even allowed access to their software development kit (SDK) packages. (Examples: Visual Studio IDE Extensions guidelines and Google’s Chrome Web Store Extensions requirements)
Why security is important for UltraEdit

Software security is an interconnected chain of defenses and failsafes.
As a commercially supported software, we believe that UltraEdit should bring confidence and peace of mind to all those who use it. In the text editor space dominated primarily by open source programs, UE has the unique advantage of having a dedicated team of developers advance, manage, and fortify all of its features right from the start, minimizing zero day vulnerabilities.
UE is a tool used by a variety of users, for many different purposes that even the creators of the tool may be unaware of. Some of these use cases may be simple everyday tasks, while others will be working with highly sensitive information or business-critical assets.
Furthermore, with ever increasing reliance on information technology, so should the standards for software. Take for example the industry shift and interruption brought about by the pandemic. Remote setups are generally more convenient but they are a security nightmare. Every employee with remote access can be an exploitable crack in your company’s security chain. Employee training and preparation is necessary but a foolproof system and software design is impeccable.
This emphasizes the importance of security, not just for a text editor, but for software in general. However, UltraEdit is committed to making sure that it will not be a cause for concern for any of its users and customers. As a result, it has become one of the best open-source alternatives that is on par in terms of versatility, but still provides the benefits of dedicated customer support and security associated with commercial software.
UltraEdit’s Security Tools and Features
Software programs and developers employ a number of tools and techniques to harden their cybersecurity. UltraEdit employs the following three-tiered approach to harden its software security:
- Manual and Peer Review
Every source code commit or edit for any of the UE tools undergoes intensive review by the developer themselves before it is passed to senior developers for scrutiny. This check filters out the most apparent and probable issues.
A company or developer without this step will have credibility issues. - Static Application Security Testing (SAST) tools
UltraEdit uses a dedicated source code analysis tool to scan source code for possible vulnerabilities. These help detect issues that are laborious to check manually. This involves filtering out common software errors such as obsolete programming techniques, memory leaks, buffer overflows, race conditions, and the like.Most companies will have SAST tools as it also provides a predictive summary of how efficient, maintainable, reliable, and portable the examined source code is. - Software Composition Analysis (SCA) tools
Next up, UE looks at its external dependencies. UE is not an open source software but it does use open source components. This is one of the more crucial steps that not every company will have. This type of scan cross-verifies each and every line in UE’s open source dependencies with a database of known vulnerabilities maintained by security professionals. This database is continuously updated so that security issues can be detected and mitigated as part of the standard product build pipeline.
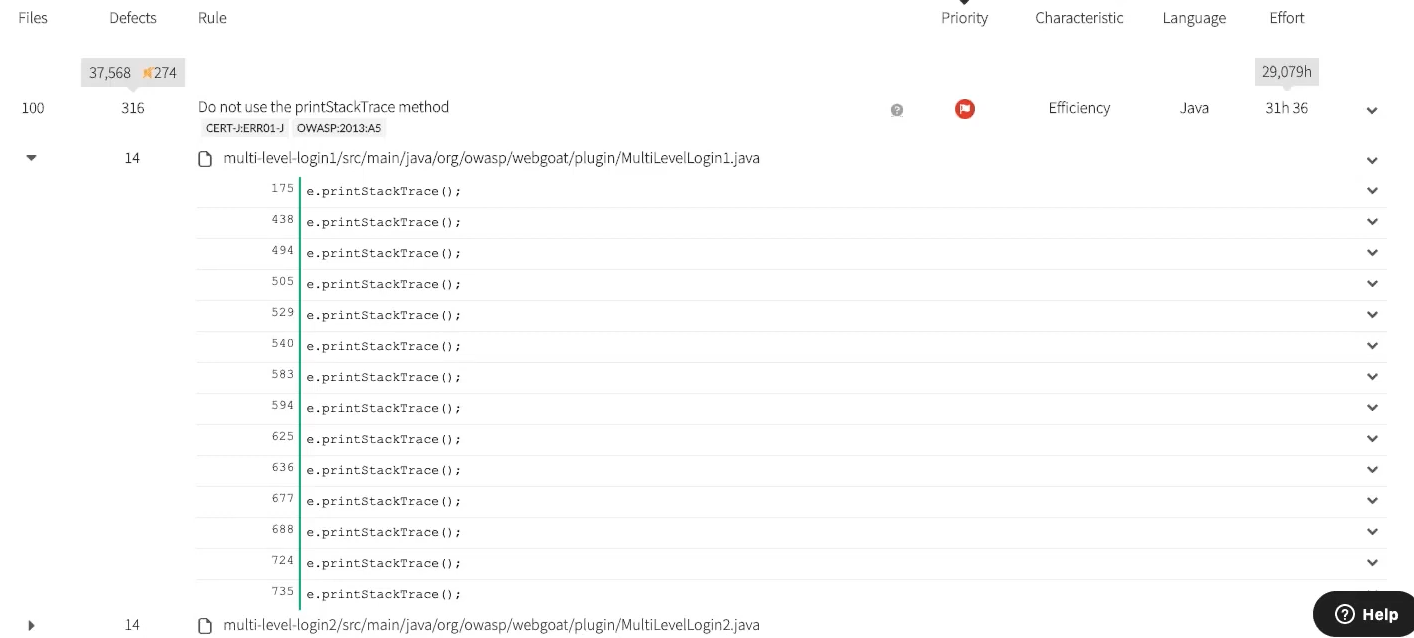
A source code analysis tool will detect issues and provide general instructions on how to fix the potential issue.
Summary
Summing up our discussion, a text editor like UltraEdit places an emphasis on security because (1) it is necessary in this day and age where every user and company is reliant on technology and (2) because our users deserve the best and most secure system possible.
The goal posts for software security continuously move forward and no single version of any software will be 100% secure. That is why it is of the utmost importance to have a robust and stringent development process for UltraEdit. This article discussed UE’s general approach to security, and there are many threats and security issues that may arise in the future, but rest assured that the UE team will provide more than complete coverage with the best available security technology.









0 Comments